A Viral Claim Sends Shockwaves Through Steam
A programming-focused MMO on Steam has found itself at the centre of a major security controversy after claims surfaced that simply playing the game could allow other players to gain remote access to your computer.
The allegation went viral after Isaac King posted on X, formerly Twitter, claiming that an MMO with more than 100,000 purchases contained a vulnerability that could let other players execute code on your machine. According to King, the issue had been reported previously, Steam had been notified, and the developer was allegedly aware of the problem.
I wrote about this in my latest article:https://t.co/vh8aHGhxQL
— Isaac King 🔍 (@IsaacKing314) January 24, 2026
The game in question was Screeps, a long-running MMO RTS where players write real JavaScript code to control their in-game units.
How The Screeps Vulnerability Worked

Image Credit: Screeps, LLC
Screeps is built around automation and scripting, with players using JavaScript to manage everything from resource collection to combat. In multiplayer worlds, players often rely on console logging to debug their code and track in-game events.
The issue highlighted in King’s article centred on how the game handled console output. Screeps allowed HTML to be rendered directly through console.log calls, including unfiltered player-supplied input such as unit names. This meant malicious code could be injected and executed when another player’s client processed that output.
While this behaviour was already risky in the browser version, it became far more serious in the Steam client. The Steam build reused browser code without proper sandboxing, meaning successful exploitation could result in full system-level access via the local machine, not just the game itself.
In simple terms, interacting with the wrong player in a multiplayer world could potentially expose your computer to remote code execution.
Community Backlash And Accusations Of Inaction
The claims quickly gained traction, with players resurfacing old GitHub reports, Steam reviews, and Discord discussions alleging that the issue had been known for years. One widely shared Steam review written by Isaac King himself described the client as insecure and accused the developers of ignoring a one-line fix while continuing to sell the game.
Criticism intensified after screenshots showed earlier developer responses denying the existence of any serious vulnerability, with some players accusing the studio of downplaying the risk and failing to warn users.
As the story spread, Screeps’ reputation took a hit, despite the game maintaining a largely positive rating on Steam.
Developers Roll Out A Hotfix After Article Goes Viral
The update now escapes HTML by default in console.log, preventing injected scripts from executing. A new console.logUnsafe method was also added for advanced users who intentionally want to log styled HTML, shifting responsibility clearly onto the player.
The fix effectively closed the exploit path that allowed arbitrary code execution in the Steam client.
Developer Response And Ongoing Dispute
Despite implementing the fix, the Screeps developers have continued to dispute the characterisation of the issue. In public statements, GitHub replies, and a Steam news post, the team maintained that they did not consider the behaviour a true vulnerability, arguing that it involved player-written code and required specific circumstances to exploit.
They also stated that they had never received verified reports of real-world harm resulting from the issue and cited limited resources as the reason the fix had not been prioritised earlier.
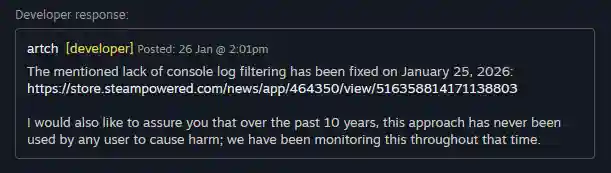
Image via Steam
At the same time, the developers acknowledged that the situation was not ideal and apologised for misunderstandings, while notifying players of the change via email, Steam, and social media.
What This Means For Players Now
With the hotfix live, Screeps is no longer vulnerable in the way described, and the Steam client is considered safe to use under the new logging system. Players who were concerned about security risks can now return to the game without needing additional safeguards.
However, the incident has sparked broader discussion about transparency, security practices, and developer responsibility, particularly for games that blur the line between gameplay and real-world programming environments.
For now, Screeps remains available on Steam, its core concept still praised by many players, but the controversy has left a lasting mark on how the community views its development and long-term stewardship.

